How should I use DSC?
In my last blog, I discussed Microsoft’s Desired State Configuration (DSC) resources and features introduced in PowerShell 4.0. In today’s post, let us explore a convenient and productive use case for DSC – enabling the Hyper-V role on servers in your domain.
Remember you first need to create a Configuration script block, which keys PowerShell that you are defining DSC resources. Think of this block as a sort of .INI set of definitions for your environment. Inside the Configuration script block, you can define blocks for servers, referred to as Nodes in your script block, which you wish to configure specifically. When you invoke your script containing the Configuration block, PowerShell creates a Managed Object Format file, MOF. It is the actual MOF files that are executed on your servers, typically using PowerShell remotely via Group Policy. The MOF files remain static until you compile new ones from changed Configuration script blocks. I think of this as a convenient way of doing a “reset” for your server configuration.
To create a Configuration to enable the Hyper-v role on your targeted host servers (Nodes), create a PowerShell script containing the following:
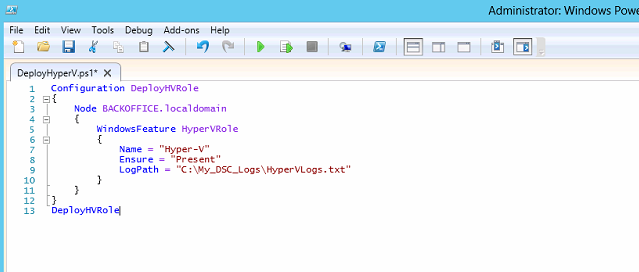
Then run your PowerShell script to create the MOF file:
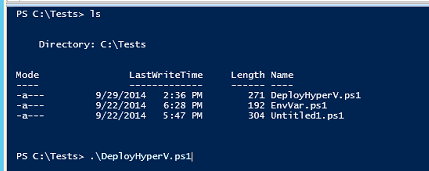
The MOF file is created in a folder with the same name you gave the Configuration block, and the MOF file is created with your <Node name> with an MOF extension.
You can use loops in your PowerShell script to create MOF files for each host you want to configure in your environment.
To execute the DSC for Hyper-V role setup, run the PowerShell cmdlet:
Start-DscConfiguration -Wait -Verbose -Path .DeployHyperV
The –Wait parameter causes the cmdlet to run interactive mode, otherwise it runs in batch mode and returns a job.
Again, leveraging DSC to maintain your compute environment can be a powerful and time-saving tool. We’ll look at other use cases in upcoming posts.