Cybersecurity has become a major priority for small and midsize businesses (SMBs) and mid-market enterprises (MMEs) alike. With data being the lifeblood of modern businesses, exposure to nefarious threats can bring operations to a screeching halt. Data loss incidents can expose sensitive client and company data and cost millions in reparations. That’s why organizations must invest both time and effort to safeguard their data from the agents of data breaches and keep cybersecurity threats at bay.
To stay ahead of the threat landscape, organizations must realize that security threats aren’t always external. According to the Verizon 2021 Data Breach Investigations Report, “insiders” are responsible for around 22% of security incidents. The ability to identify and mitigate the risks posed by insider threats is just as important as taking care of those that originate externally.
Read on to learn about the dangers insider threats pose to your business and how to defend against these threats.
What are insider threats?
Insider threats are security risks that originate from within an organization. These incidents involve individuals with legitimate access to an organization’s network and systems who misuse or abuse their access to cause harm. The harm comes by way of malicious or unintentional acts that compromise an organization’s integrity and confidentiality.
An attack from an insider can lead to data corruption or damage, espionage, sabotage, cyberterrorism and unauthorized information disclosure. It can also allow cybercriminals to launch malware or ransomware attacks.
Due to their familiarity with enterprise systems and the valid authorization to data, insider threats are difficult to detect. In most cases, they go undetected for months or years. As a result of this subterfuge, more than 34% of businesses worldwide are affected by insider threats every year.
It is critical for security teams to develop insider threat detection methods that can prevent the exposure of sensitive information by threat actors and negligent insiders. In those cases, it is crucial to have a distinct understanding of which individuals and actions could be deemed an insider threat.
What constitutes an insider?
An insider can be any individual with authorized access to your organization’s sensitive information, including personnel, facilities, equipment, networks and systems. Anyone can be an insider threat — your employees, contractors, vendors or any repair person who has access to company devices or assets.
Individuals who possess institutional knowledge about your organization’s fundamentals, including pricing, costs, strengths and weaknesses, also fall under this category. This also includes people who have insights into your organization’s strategy and goals, and are entrusted with future plans, thereby giving them access to protected information.
What causes insider threats?
The causes for insider threats can vary significantly. The ones that are malicious in nature are often motivated by money, a competitive edge or revenge. However, not all insider threats are malicious. Some threats are careless (accidental) in nature.
Here are some of the most prevalent reasons for the occurrence of insider threat activity.
Ignorance
A general lack of awareness of the present cybersecurity landscape is the primary reason why many people unintentionally compromise sensitive data. This might happen because of inexperience or the person is unaware of the company policies. A small percentage of people who don’t respond to the security awareness training add to such problems.
Negligence
Negligence is one of the most common reasons for an insider threat incident. When someone willfully neglects to adhere to an organization’s security policies and protocols, the chances of an insider threat incident increase. An individual might store intellectual property on an insecure personal device, triggering security risks.
Financial motivation
Accessing sensitive information about an organization and then leveraging it in a nefarious way for financial gain is another common ploy malicious insiders adopt. Here, the insider might install malware, or intentionally leak confidential data to others or on the internet for monetary gain.
Emotional motivation
Like money, emotion can also be a driving force to carry out such incidents. A recently fired employee can sell sensitive data to a competitor as an act of vengeance, or a disgruntled employee can deliberately sabotage security tools and controls. An emotionally motivated insider can even steal intellectual property for personal benefit.
Political motivation
Although politically motivated incidents are less frequent, there are several cases of state-sponsored insider threat attacks and corporate espionage. National sentiments and political indoctrination can be considered the primary drivers in this case.
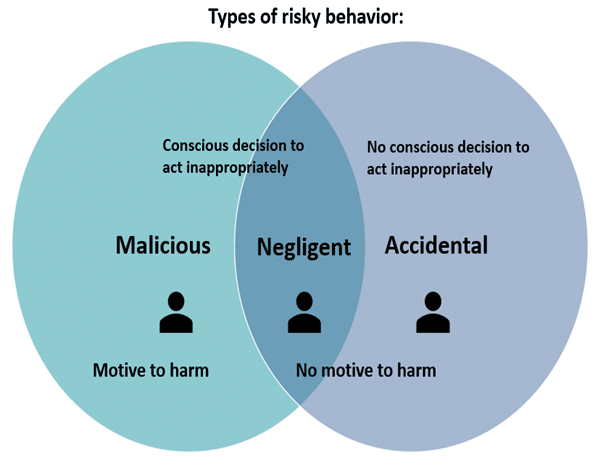
What are the three types of insider threats?
Insiders can vary based on their motivation, awareness, amount of access and intent. Most insider threats can be classified under the following labels or personas:
Malicious insider
They are also referred to as turncloaks and intentionally abuse their privileged access to steal information or disrupt systems for monetary or personal reasons. Espionage, fraud, intellectual property theft and sabotage are the primary drivers for these actors.
Collaborator
These are authorized users who cooperate with outsiders, like a competitor of their current company, organized crime network or nation-states. They steal intellectual property and customer info and disrupt business operations.
Lone wolf
As the name suggests, they prefer to operate independently and act without external manipulation or influence. They often have privileged system access, such as database admins, and that’s what makes them so dangerous.
Careless insider
These unintentional threats occur when data is lost or stolen due to employee negligence or error. Individuals involved in such cases unknowingly expose enterprise systems to external attacks, leading to data leakage, security attacks or stolen credentials. They can also fall victim to phishing and other social engineering tactics.
Pawns
These are employees who get manipulated without knowing into acting maliciously. This often happens through social engineering tactics that could include downloading malware to their computer or disclosing confidential information to an imposter.
Goofs
These are ignorant, incompetent and arrogant users who don’t recognize the need to follow security policies and procedures. They try to bypass security controls and, as a result, leave vulnerable data and resources unsecured, giving attackers easy access.
Compromised insider (Mole)
This is an outsider who has gained insider access to an organization’s systems by posing as an insider. They may pose as a vendor, partner, contractor or an employee and get privileged authorization, which wouldn’t be possible to obtain as an outsider.
How are insiders taken advantage of?
Threat adversaries often focus on spotting the weak link in the security chain to carry out their activities, employing a variety of strategies and techniques with the goal of obtaining valid credentials. This includes phishing emails, watering holes, weaponized malware and many more. They may also look for rogue insiders and collaborate with them to gain access to enterprise systems. Threat actors rely on financial, emotional or political motivations to manipulate their targeted insiders.
Threat actors mainly attack in the following way:
- Identify vulnerabilities
- Use phishing emails or viruses
- Identify rogue user(s)
- Obtain credentials that have been hacked
- Leverage the access option to the fullest
- Travel laterally toward the targeted goal
- Elevate the privileges
- Gain access to sensitive data with those credentials
- Abuse the access
- Obfuscate network activity
- Change the data
- Exfiltrate information
What are some indicators of insider threat behavior?
A focus on analyzing network, devices and application data is essential to maintain a secure cyber defense against insider threats. It’s equally important to keep a close tab on the actions of authorized persons who could misuse their privileged access. Monitoring both anomalous behavior and digital activity is essential.
Here are some telltale signs to be aware of:
Unusual conduct or work schedule
If any employee is regularly working off-hours or displaying disgruntled behavior towards colleagues, then it needs to be addressed. Carrying resentment towards co-workers can lead to a lack of passion for work and negligence in keeping data secured while working. Often, while working at odd hours, people tend to make errors and end up clicking on phishing emails or storing sensitive information erroneously.
Poor performance reviews
Poor performance reviews of an employee can be a sign of negligence or disengagement. The individual risks accidentally exposing protected data or falling victim to any social engineering tactics. Such individuals can be easily manipulated for financial or emotional gain.
Policy and procedural disputes
There are users who often push back against authority due to differences in their approach to doing things. They can be financially or emotionally motivated by any threat adversaries to carry out nefarious activities.
Unnecessary activity or access requests
People who perform unusual tasks that don’t fall under their job profile or someone who requests access to data or resources outside of their job scope are certainly cause for concern and could possibly be insider threats.
Defying security protocols
There are people who often circumvent security policies laid out by their organizations as safety measures. Such acts should not be entertained, and the individual(s) must be educated on the importance of security policies and procedures and persuaded to follow them.
Resigning or looking for new opportunities
An employee looking for a new opportunity or on notice period can sometimes download all work files and data on unauthorized storage devices or send them to their personal email. Such an exercise can be detrimental to the company.
What are some examples of insider threats?
While numerous insider threat incidents take place every year, here are some incidents that stood out in recent years.
In 2021, Juliana Barlie, an employee of an undisclosed credit union in New York, destroyed more than 20GB of data, including financial records, in retaliation for being fired.
In 2020, a former Google executive was sentenced to 18 months in prison for trade secret theft and selling them to a competitor.
Instances like these prove how serious insider threats can be.
Insider threat statistics
Security incidents due to insider threats have increased considerably. In the post-pandemic era, most employees prefer the hybrid work model. Employers, however, are skeptical about this model, with many believing their organization is at greater risk of insider threat attacks if the company adopts a permanent hybrid work structure. Around 66% of organizations consider malicious insider attacks or accidental breaches as a more likely outcome than suffering an external breach.
Insider attacks are expensive to organizations as well. According to the 2022 Cost of Insider Threats Global Report by the Ponemon Institute, the average annual cost of an internal data breach is $15.38 million, with 56% of those incidents attributed to negligent insiders.
What is the impact of insider threats?
Insider threats can have a deep impact on an organization. It can directly impact revenue, causing organizations to lose a chunk of their revenue in an incident. As a result, the market value of the organization can diminish to a great extent.
Increased overheads due to cybersecurity improvements, staff retention and other factors can adversely impact business operations. Theft of intellectual properties like new product designs and strategies can also have huge repercussions since they can damage an organization’s reputation.
How are insider threats prevented?
The specter of insider threats can be kept at bay by constantly monitoring user activity, gaining real-time insights into network activity and taking fast and effective action when a security incident occurs.
Following this four-step security event method can go a long way towards preventing insider threats:
Detect
Organizations must detect malicious, suspicious or unusual activity on their networks. Having real-time insights into user logins and the locations they have logged in from helps improve network visibility and track employee actions.
Investigate
When suspicious activity is detected, organizations must investigate immediately. Time is of the essence in such cases since malicious insiders can move swiftly to carry out their attacks.
Prevent
After determining whether the suspicious activity is malicious or unauthorized, organizations must prevent malicious users from gaining access to their networks and systems. They can also prevent insider threats by deploying virtual private networks (VPNs) to encrypt data to help users keep their browsing activity anonymous.
Protect
By enforcing security policies and securing data, organizations can protect their users and devices. Critical assets, such as facilities, people, technology, intellectual property and customer data must be protected at all times with proper levels of access rights and privileges. Policies must be clearly documented, and employees should be familiar with security procedures while complying with stringent data privacy regulations.
Best practices to keep insider threats at bay
Here are some safe practices that can be deployed to counter insider threats.
Protect critical assets
Understanding critical assets and then prioritizing them for protection is necessary. Comprehensive knowledge of the current state of each critical asset is required.
Enforce policies
Documentation of organizational policies helps in preventing misunderstandings. Everyone in the organization must be familiar with security procedures and should understand their rights concerning intellectual property.
Increase visibility
Organizations must deploy solutions to track employee actions and correlate information from multiple data sources.
Promote culture changes
Security is not only about knowhow but also about beliefs and attitudes. Address the drivers of malicious behavior to combat negligence. There’s a need to improve employee satisfaction and carry out security awareness training.
Technologies to combat insider threats
To protect assets from insider threat attacks, the threat detection strategy must not rely on a single approach. An effective solution, in this case, consists of a combination of several tools that monitor inside behavior and filter through many alerts to eliminate false positives.
A security information and event management (SIEM) solution can be used to aggregate, normalize and interpret the vast data feeds from monitoring solutions. Additionally, developing and implementing a privileged access management (PAM) solution provides a thorough approach to user privileges and access rights, thereby minimizing data exposure.
Protect against insider threats with Unitrends
Any business with an online presence in today’s digital world carries the risk of data compromise. Irrespective of company size, insider threats can wreak havoc by exposing confidential information. A robust cyber resilience strategy is required to prepare for and effectively respond to such threats.
Unitrends Unified BCDR, an all-in-one backup and recovery solution, provides comprehensive protection against data loss caused by malicious insiders, careless employees, cyberattacks and more. It enhances your organization’s cybersecurity posture and enables business continuity with built-in threat detection, immutable backup and automation that allows for rapid recovery after an attack.
Find out how Unitrends can help you thwart the risks of insider threats and build a more resilient business.