
FIPS Mode for Unitrends
FIPS Mode for Unitrends delivers cyber resilience for regulated and compliance-driven environments.
Ransomware Resilient Backup and Recovery
of CISOs admit they do not know where some or all their data is or how it’s protected1
1Help Net Security, “CISOs’ Priorities for the Coming Year,”
Mission-critical data now lives in more places than ever before — data centers, multiple clouds, SaaS applications and endpoints — but one constant remains, it’s under attack. Our mission is to eliminate the stress of downtime and data loss with a security-first solution which ensures your data is always awailable, always secure.
Cybercriminals predominantly target Windows-based devices. When those attacks occur, your Windows-based backup solution (and backups!) are also vulnerable. Unitrends is Linux-based, which reduces the risk of compromise.
Identify potential ransomware activity through proactive monitoring utilizing proprietary behavioral analytics. Run against every backup, Unitrends immediately alerts admins upon detection of early signs of infection.
Ransomware threat actors increasingly target users with phishing, brute force and account takeover attacks to gain access to systems and networks. Proactively secure users and accounts at risk with integrated Dark Web monitoring.
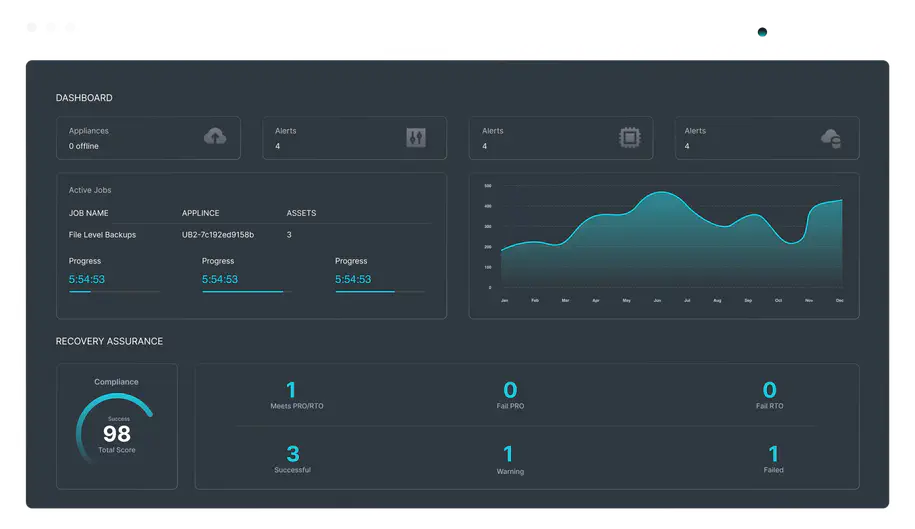
Simply schedule the time and systems you want tested and we do the rest. If tests show that you can’t meet your SLAs, simply make adjustments in your backup process and re-run the tests to check the changes. Learn more about Automated Testing.
Automatically identify and fix Windows issues in your production environment (like VSS errors) before they have a chance to impact a successful backup.
Ransomware is targeting backups - working to disable them from happening, encrypting them, or deleting them all together. With Unitrends, data is stored in an immutable format, meaning ransomware cannot access or compromise your backups. Your data is safe and always recovery ready.
Unitrends turnkey, appliance-based solution is immune to AD, Virtual Host and Windows-Based Attacks
“We were fully functional by Monday morning. Quite honestly, I don’t know what would have happened to the company if we didn’t have Unitrends.”
Take the first step in your transformation. See it live.
Request a Demo
FIPS Mode for Unitrends delivers cyber resilience for regulated and compliance-driven environments.

Learn more about Unitrends cloud storage and disaster recovery-as-a-service (DRaaS) offerings – available for Recovery Series appliances and Unitrends Backup software.

The Disaster Recovery Planning eBook provides key insights and best practices for protecting critical data and ensuring business continuity under any circumstance.