The Latest Trends in Devastating Cyberattacks
Cyberattacks are a harsh reality in today’s digital-first landscape. Despite the overall improvement in cybersecurity capabilities and awareness among organizations worldwide, the threat and sophistication of attackers has kept pace and, in some cases, exceeded the progress made with regard to cyber defenses. With rapid digital transformation and the growing trend of remote and cloud-based work, cybercriminals are increasingly targeting small and medium-sized businesses (SMBs).
A recent CSO Online report revealed that a staggering 84% of code bases have at least one open-source vulnerability. Hackers, and particularly ransomware gangs, take advantage of these flaws to carry out zero-day exploits to wreak havoc.
The cyberthreat landscape: Facts in figures
Cyberattacks have become inevitable this day and age. It’s no longer a matter of “if,” but rather “when” an attack will take place The staggering rise in the total cost of a data breach is a testament to the ferocity and efficacy of such attacks. IBM’s Cost of a Data Breach Report 2023 found that the global average data breach cost rose to $4.45 million in 2023 — a 15% increase over the last three years.
Among the common root causes of these data breaches, phishing and stolen or compromised credentials are the two most prevalent initial attack vectors (16% and 15%, respectively). They are also ranked among the top four costliest attack types. The costs of both phishing and stolen or compromised credential incidents were reported to be $4.76 million and $4.62 million respectively, which is higher than the global average cost of a data breach cited earlier.
When it comes to identifying the breaches, only one-third were identified by the organizations’ internal security teams and tools. Data sprawl has a part to play in this. The monitoring and visibility of data across a distributed environment is challenging, and hackers are smart enough to exploit this loophole. The outcome? Rampant ransomware attacks. As per IBM, around 27% of breaches were disclosed by attackers as part of a ransomware attack. In these situations, remediation cost organizations $1 million more as compared to internal detection.
Although ransomware incidents have been hitting the headlines, it is not the most frequent attack observed by IBM’s researchers. This year, destructive attacks, which render systems inoperable and make data recovery difficult, accounted for 25% of all malicious incidents — slightly edging out ransomware (24%) for the top spot.
Destructive attacks on hybrid environments
Recent destructive attacks have involved threat actors disguising their attacks as standard ransomware campaigns. This easily dupes victims into treating the attack as a ransomware incident while attackers carry out destruction and disruption unchecked — the ultimate goal of such campaigns. Microsoft recently detected one such campaign, deemed more devastating than ransomware attacks. This destructive operation was carried out by MERCURY, a state-sponsored threat actor that attacked both on-premises and cloud environments.
Partnering with DEV-1084
In this campaign, MERCURY is said to have worked with another actor tracked as DEV-1084, who carried out destructive actions once MERCURY gained access to the target environment. Known vulnerabilities in unpatched applications were likely exploited to gain initial access before handing it off to DEV-1084. From there, DEV-1084 then performed extensive reconnaissance and discovery. The attackers moved laterally through the network, waiting weeks, sometimes even months before moving to the next stage.
Post initial compromise
It was found that DEV-1084 leveraged highly sensitive compromised credentials to carry out high-volume destruction of resources. The targeted resources included server farms, virtual machines, storage accounts and virtual networks. Emails were also sent to internal and external recipients. Once the initial compromise was complete, DEV-1084 deployed web shells, created administrative user accounts, installed legitimate tools for remote access (such as RPort, eHorus and Ligolo), planted a customized PowerShell script backdoor and stole credentials.
Tools and techniques
Once these actions were carried out, continued access to compromised devices was maintained. This allowed the bad actors to leverage native Windows tools and commands like netstat and nltest to perform extensive reconnaissance activity. They also executed lateral movement actions using the credentials acquired within the targeted environment. Hackers carried out these activities via:
- Remote scheduled tasks for launching the PowerShell backdoor.
- Windows Management Instrumentation (WMI) for launching commands on devices.
- Remote services to run PowerShell commands.
After each main attack step, the threat actors waited weeks or months before progressing. Several C2 servers were leveraged for the effective execution of the campaign, followed by the deployment of tunneling tools, such as Ligolo and OpenSSH, to stay undetected by security teams and solutions.
Extent of devastation
As part of the installation procedure in the early stage, multiple accounts were created in the on-premises (Windows Server Active Directory) and cloud (Azure Active Directory) environments. When moving from on-premises to the cloud, threat actors compromised two privileged accounts to manipulate the Azure Active Directory (AD) Connect agent (see Figure 1).
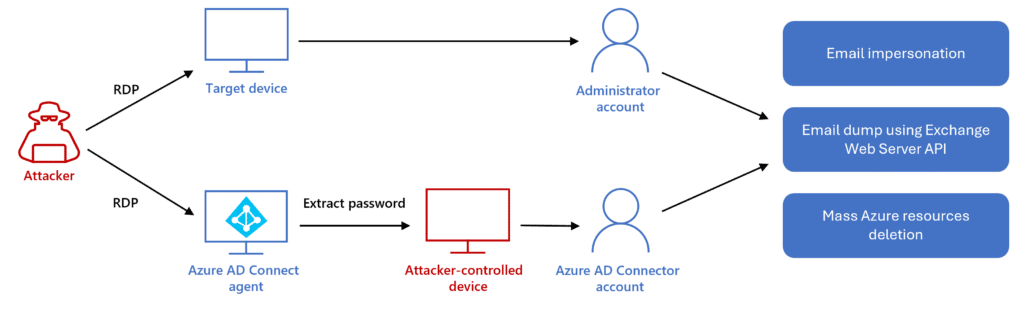
Figure 1. The attack flow when threat actors pivot to the cloud. (Source: Microsoft)
The first one was the compromised Azure AD Connector account with Global Administrator permissions. The second account, which also had Global Administrator permissions, was accessible by the threat actors via Remote Desktop Protocol (RDP). The attackers evaded the multifactor authentication (MFA) in place with the help of the RDP, easily gaining entry and elevating privileges.
The attackers’ main goal was believed to be the infliction of data loss and a denial of service (DoS) of the targeted environment’s services. With the help of these compromised accounts, the bad actors obtained credentials for other privileged accounts and exploited them for other malicious activities. This included updating the OAuth application with certificates for malicious purposes and attempting to dump mailboxes and/or search for sensitive data in them.
Reducing the impact of such attacks with Unitrends
A destructive attack of such a level can have a huge financial impact on the total cost of a breach. Also, factors like remote workforces and a shortage of security skills amplify data breach costs significantly. That’s why organizations need to carry out various actions to limit the exposure of data and lessen the impact of such cyberattacks. This is where Unitrends Unified Backup comes in handy.
As per the IBM report discussed above, high-level incident response planning and testing can reduce breach costs by $232,000 on average. Unitrends can play a big role in this with its Recovery Assurance automated recovery testing and efficient, affordable Disaster Recovery-as-a-Service (DRaaS) solution. Moreover, the ransomware detection capabilities of Unitrends, driven by artificial intelligence and machine-learning-driven insights, carry out proactive detection to identify attacks early. This enables organizations to respond proactively to malicious activity, reducing the amount of data compromised and the overall impact of the attack.
Unitrends also helps protect users and credentials with powerful, multilayered phishing defense and integrated dark web monitoring for compromised or stolen credentials as part of Spanning, our cloud-to-cloud backup solution for SaaS applications.
Unitrends Unified Backup truly is an all-in-one backup and disaster recovery solution you can rely on. But don’t just take it from us! Thousands of organizations across the globe depend on Unitrends for their data protection needs — from school districts to manufacturing, technology solutions providers and more. Want to know how Unitrends could be the answer to your data loss and downtime worries? Book a call with us today!